Breaking S/KEY
One time passwords are intended to protect against "shoulder surfing" attackers. The observation of a successful OTP login should not help an attacker to gain future access to a system.
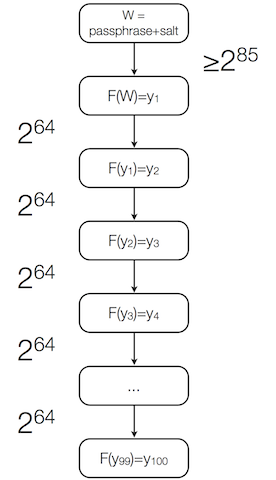
It is well known that the serial dependency of one time passwords in systems based on Lamport's scheme (e.g. S/KEY) is an attribute that trivially reveals previous passwords. It is commonly overlooked though that the observation of a successful login also enables an attacker to perform an off-line attack on the next password.
We note that an attacker does not need to attack the salted master pass-phrase of the hash chain. Instead it can be sufficient to reverse the unsalted last segment of the hash chain that leads to the observed one time password.
The specifications of the RFC 1760 (S/KEY) and RFC 2289 (OTP) authentication systems do not offer sufficient protection against such attacks. Implementations of these and similar systems can be found in operating systems (e.g. OPIE(4), PAM_OPIE(8), and SKEY(1)) and network applications (e.g. SASL and RFC 2444).
Talks:
In August 2013 I gave a lecture about "Breaking S/KEY" at OHM2013 in the Netherlands. The slides are available here.In September 2013 I gave a slightly updated lecture with the title "The practical weakness of the S/KEY one-time-password system (RFC 1760 and 2289) against brute force attacks" at the EIPSI Crypto Working Group meeting in the Netherlands. The slides are available here.